Forward Proxy VS Reverse Proxy.
The position of a proxy — is what makes a proxy either a forward or reverse proxy. The easiest way to remember the difference between these two proxy is - Forward proxy is used by clients where as Reverse proxy is used by servers. Let us jump into it.
Forward Proxy
A forward proxy, also known as a proxy server or web proxy, sits between client machines and the Internet, intercepting outgoing requests.
When clients attempt to access websites or online services, the proxy server processes these requests on their behalf before relaying them to the destination servers.
Acting as an intermediary, a forward proxy helps control and secure client-side traffic, often working alongside a firewall to enforce network policies.
Its primary security function is to regulate and protect internal network clients by filtering access, anonymizing requests, and preventing direct exposure to external threats.

Clients 1, 2, and 3 send their requests to the Proxy Server instead of directly reaching the destination server. The Proxy Server then forwards these requests over the internet to the Destination Server, retrieves the responses, and sends them back to the clients. This setup is commonly used for anonymity, content filtering, and access control.
In standard Internet communication, a user's computer directly connects to a target server, sending requests and receiving responses.
However, when a forward proxy is used, the user's requests are first sent to the proxy server, which then forwards them to the target server. The target server processes the request and sends the response back to the forward proxy, which, in turn, relays it to the user.
This setup helps with security, anonymity, and access control by ensuring that the target server only interacts with the proxy rather than the user directly.
Why add an extra middleman to Internet activity?
Just like in many aspects of life, there are several reasons why someone might choose to use a forward proxy:
1. Anonymity & Privacy
• Hides client IP addresses from destination servers.
• Prevents websites from tracking users directly.
2. Access Control & Web Filtering
• Blocks access to restricted or malicious websites.
• Enforces company policies on internet usage.
3. Security & Malware Protection
• Scans and filters traffic to block malicious content.
• Prevents direct access to dangerous websites.
4. Bandwidth Optimization & Caching
• Stores frequently accessed content to reduce bandwidth usage.
• Speeds up content delivery by serving cached responses.
5. Geo-Restriction Bypass
• Allows users to access region-locked content.
• Routes traffic through different locations to appear as if from another country.
6. Logging & Monitoring
• Tracks user activity and internet usage for compliance.
• Helps organizations analyze and optimize network performance.
7. Content Compression & Optimization
• Reduces data usage by compressing web pages.
• Speeds up browsing for slow connections.
8. Load Distribution for Outbound Requests
• Balances outgoing requests across multiple IPs.
• Reduces the chance of IP blacklisting.
9. Corporate & Educational Network Management
• Ensures employees or students adhere to internet usage policies.
• Prevents access to non-work-related sites.
10. Security in Untrusted Networks
• Protects users when browsing on public or insecure networks.
• Adds an extra layer of security for sensitive connections.
Reverse Proxy
A reverse proxy is a server positioned in front of one or more web servers, intercepting client requests while keeping the backend servers hidden.
Unlike a forward proxy, which sits in front of clients to manage outbound traffic, a reverse proxy handles inbound requests to backend servers.
When clients attempt to reach a website's origin server, their requests are first intercepted by the reverse proxy within the network. From that point on, the proxy manages all communication between the client and the backend servers.
By acting as an intermediary, a reverse proxy enhances security, improves load balancing, and shields backend infrastructure from direct exposure.
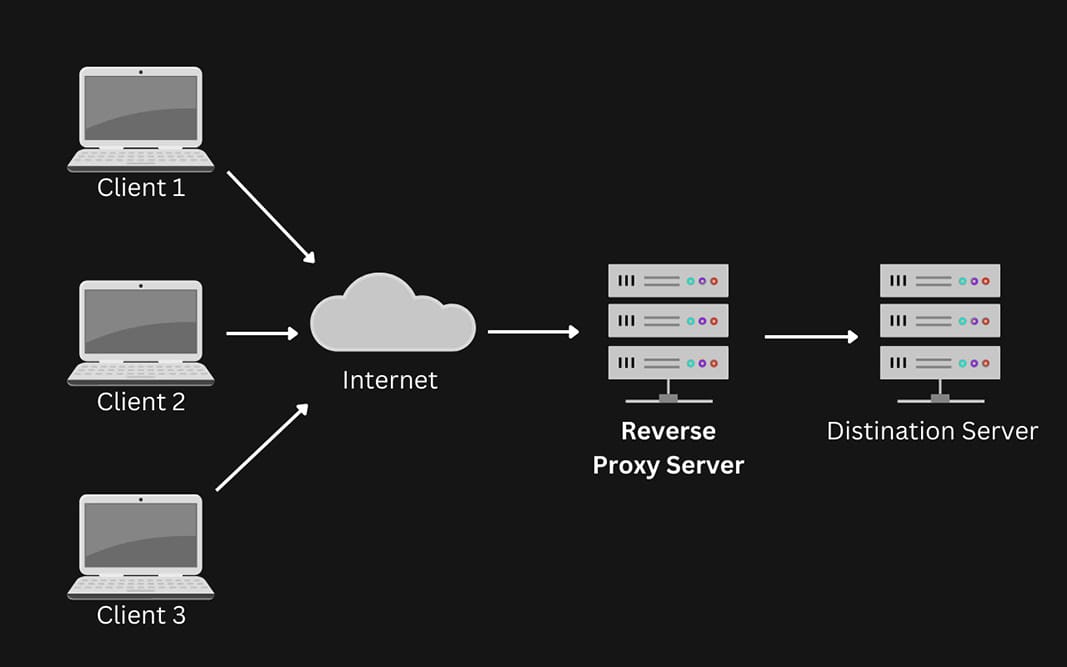
Typically, all requests from Clients 1, 2, and 3 would go directly to Server 1 or Server 2, and Server 1 or Server 2 would send responses directly back to Clients 1, 2, and 3.
With a Reverse Proxy, all requests from Clients 1, 2, and 3 will go directly to the Reverse Proxy instead of the backend servers. The Reverse Proxy will then determine which server (Server 1 or Server 2) should handle the request, send it to the selected server, and receive the response.
Finally, the Reverse Proxy will pass along the appropriate responses to Clients 1, 2, and 3.
Here, we outlined some of the benefits of a reverse proxy:
1. Security & Anonymity
• Hides backend server IPs from the public, reducing attack surface.
• Can filter malicious traffic, block IPs, and prevent direct server access.
2. SSL Termination
• Offloads SSL/TLS encryption from backend servers, reducing their processing load.
• Centralizes certificate management for easier maintenance.
3. Load Balancing
• Distributes incoming traffic across multiple backend servers.
• Improves availability and prevents overload on a single server.
4. Caching & Performance Optimization
• Caches static content (images, CSS, JavaScript) to reduce load times.
• Compresses and optimizes data for faster delivery.
5. DDoS Protection & Rate Limiting
• Can detect and mitigate Distributed Denial of Service (DDoS) attacks.
• Implements rate limiting to prevent abuse from excessive requests.
6. Authentication & Access Control
• Adds an extra layer of authentication before requests reach backend servers.
• Restricts access based on IP, headers, or authentication methods.
7. Web Application Firewall (WAF) Integration
• Filters malicious requests (SQL injection, XSS, etc.).
• Protects backend applications from common security threats.
8. Compression & Traffic Optimization
• Compresses responses using Gzip or Brotli to reduce bandwidth usage.
• Optimizes image delivery for different devices.
9. Seamless Backend Failover & Redundancy
• Detects server failures and reroutes traffic to healthy servers.
• Ensures high availability for critical applications.
10. Multi-Domain & Path-Based Routing
• Hosts multiple websites or applications on the same IP.
• Routes traffic based on domain names or URL paths.
That's about it!
Thank you for reading, and I hope you enjoyed this article.




